Home » The Anatomy of a Phishing Email: How to Spot Red Flags and Stay Safe
By Cian Fitzpatrick | 20th June 2024
It’s old news that email phishing is the number one culprit of security breaches.
Phishing emails account for 67% of all cyber espionage. But the silver lining is that phishing awareness is growing and the cybersecurity community is taking fiercer action in combating this form of crime.
As a cybersecurity professional reading this, you might be starting to feel a sense of a growing global support network. The pressure on security personnel has always been enormous and this is acknowledged by security vendors to a greater extent nowadays.
Unfortunately, the weakest link for cybercriminals is us. Each and every one of us.
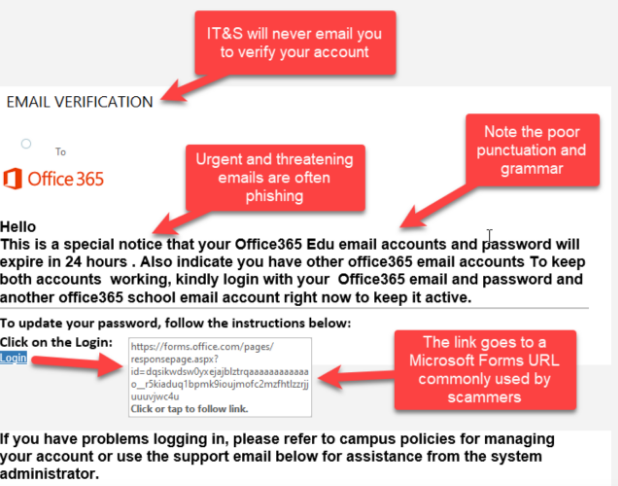
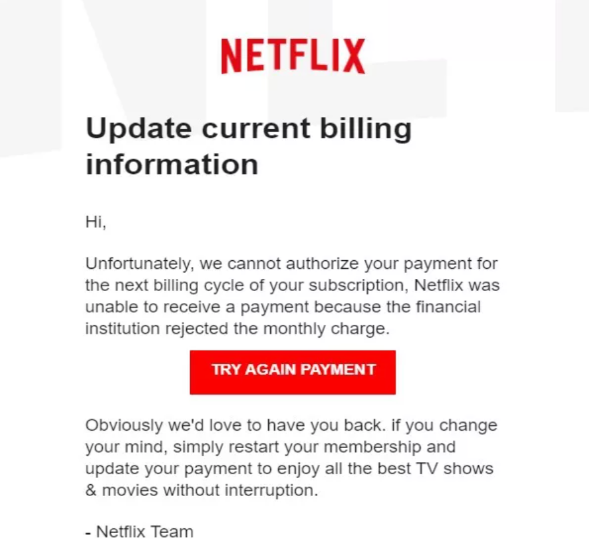
Human fallibility, gullibility, ignorance, negligence – these are universal traits. This makes each of us a cybercriminal’s target market. “Social engineering” is the term used to describe how we’re manipulated and deceived into providing access to a system or providing information or data directly. These manipulation tactics include things like urgency (‘respond within 24 hours, or else…’), greed (‘get this €100 item for just €30’), fear (‘your bank account has been hacked’), compassion (on social media, a message from a ‘friend’ – a cloned profile – in ‘urgent need of money’). And while many of these warning signs are old-hat for IT professionals, it’s easy to forget that users need to be regularly reminded of these, and other red flags.

Other red flags include unusual or incorrect grammar or strange turns of phrase.
Scammers tend not to be English first-language speakers, who use translation programmes, leading to some suspiciously odd language. When poor language is combined with the tactics previously described, chances are high that the email is fraudulent. Add in a link, or attachment, and the message is: Be Careful! A scammy URL is often fairly easy to spot, if you know what to look for. The domain name might be different to the supposed company name, or spelt slightly differently, or with numbers, a prefix, or without the HTTPS protocol. Graphics in a scam email may be of poor quality or even show inconsistencies with the actual branding.
Emails from senior staff requesting information or access details should also be viewed with caution. There’s nothing like picking up the phone and checking before responding and users should be encouraged to check with their IT colleagues if an email is suspicious before taking action.
In a report earlier this year, it was found that cybercrime cost the UK economy £30.5bn last year, with 1.5m businesses being affected. Small-to-medium businesses were 42% more under attack and costs related to cybercrime rose by almost 400%. Large businesses and one-man businesses experienced a slight decrease in attacks, although the related costs didn’t decrease. And the main culprit? Phishing.
While the direct cost of an attack can be pretty accurately calculated, it’s the reputational cost, the cost on employees’ health, enduring brand damage, and so on, that’s impossible to quantify.
Phishing prevention training is crucial for staff right now. This includes not just theoretical training, but also phishing attack simulation training. It’s important to note that there is an “acceptable” failure rate in each industry that acts as a benchmark for security testing programmes. Ideally, there would be no acceptable failure rate, but the fact is, some people will fail, and will require further training.
Cybersecurity teams are under enormous pressure currently. With a keen focus on online security, the spotlight is firmly on this department. But it’s important to know that there is support.
Our Managed Phishing Awareness Training solution offers your business the following:
Topsec’s team is focused not only on developing and maintaining security systems, but also on supporting the experts out in the field.
Contact us today to learn more.
